Worthless Capture
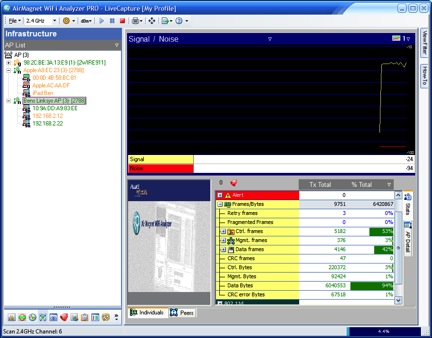
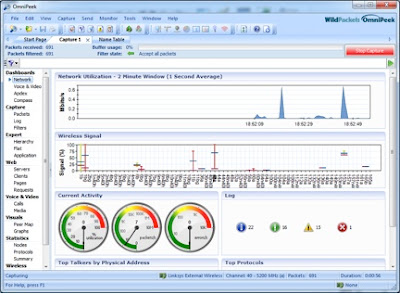
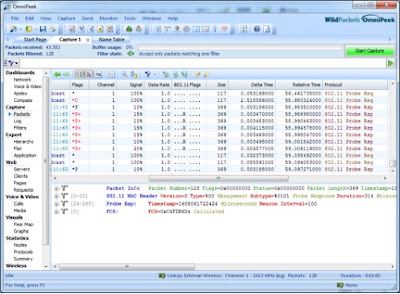
You're never gonna sniff again Faulty packets got no meaning Though it's easy to pretend I know I'm not a fool Oh, how I want to sing those lyrics . To whom, you ask? Why, to Cisco Clean Air access points. Also, AirMagnet Enterprise sensors, Aruba Air Monitors and anything else that offers me a careless whisper worthless capture. Unlike WHAM! , distributed WLAN analysis is in. It seems that nowadays I can't swing a dead cat without hitting someone who is proud as punch of their system of distributed sensors that does something (spectrum analysis, intrusion detection, frame capture) cool. Distributed sniffing (meaning frame capture) or spectrum analysis does have its uses. If you need to find a rogue AP, identify a denial of service attack or get a general overview of your RF environment, systems like Cisco CleanAir, Fluke AirMagnet Enterprise and Aruba AirWave RAPIDS can all be useful. The problem is that these products are often used for more than that. An