Here's One Eye P.A. That Won't Give You Bowel Cancer
You say you like WiFi Sniffing? And having fun? And not succumbing to a painful demise due to liver sclerosis? Well, then there's only one product pronounced eye-pee-ay for you: Metageek's new visual protocol analyzer, Eye P.A.
Amid all of our divisions over race, gender, religion and whether the Champions Bowl is going to be better than the Rose Bowl, we can agree one one thing: products named after alcohol are great. So you can imagine my excitement when I was made aware that Metageek -- hero to Windows users, villain to Mac users and tease to iPad users -- had introduced a WiFi sniffer.
Metageek is known 'round these parts ("round these parts" being, "in my opinion" ) as being a proprietor of low cost, attractive WLAN analysis tools. InSSIDer is the best active site surveying utility I've seen for Windows. The WiSpy/Chanalyzer combination is my spectrum analyzer of choice. (And I'll just choose to ignore the iPad tease that has been going to dang near a year now.) Eye P.A. is Metageek's entry into protocol analysis, and if nothing else it is quite unique.
Eye P.A. is different from most sniffers in that it doesn't sniff. Eye P.A. relies on saved capture files procured by other sniffers. Currently, the capture must be in the .pcap format and the capture must include an 802.11 Radiotap header. If you are a Linux or Mac user, a monitor mode capture from Wireshark will get you what you need. If you are a Windows user, you're going to need to spend at least seven hundred bucks on a Riverbed AirPcap NX USB adapter (or less than $700 on a cheaper AirPcap USB adapter, but then you'll miss 802.11n traffic).
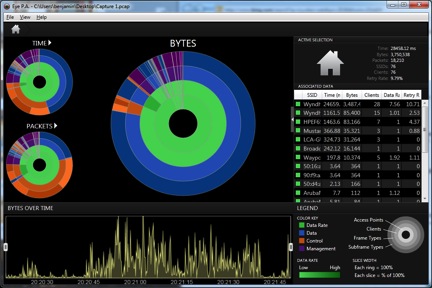
Once a capture in the .pcap format (including 802.11 Radiotap) header is made, Eye P.A. will be able to open the file. Here is a screenshot showing what Eye P.A. looked like when I opened a capture that was taken from a hotel I was staying at a short while back:
The bright orange area of the outer circle in the Packets view above are the acknowledgment frames for my laptop. The purple area of the outer circle in the Packets view are the data frames. Those two parts of the circle are about equal in size, indicating that my laptop is not a hidden node from the location where I captured. (That makes perfect sense, of course. I captured traffic using an AirPcap NX adapter that was attached to my laptop, so there is no way that my laptop's internal WiFI adapter would have been far enough away to be a hidden node.)
Eye P.A. does have usefulness in identifying hidden nodes and getting a general idea of what's taking up your channel space, but the big question is whether it is worth the $499 retail price. I think the software would be worth it for a lot of people who have to manage WiFi networks, but who feel overwhelmed by the amount of statistical information given by the average protocol analyzer. I especially like the Time circles, which use a method of calculation that factors in the amount of time taken up by the PLCP header. I could see someone who has a problem area just taking a Macbook to the problem area, doing a .pcap capture using Wireshark or Wi-Fi Diagnostics and then doing a few quick clicks or mouseovers to get a general idea of what could be the problem (over-deployment of APs, low rates to/from a station, hidden nodes, etc.). Then once Eye P.A. points someone in the right direction, a real-time WiFi sniffer like AirMagnet WiFi Analyzer or WildPackets OmniPeek could be used to pinpoint the problem and test whether an attempted solution works.
The bottom line is that Eye P.A. is a fine compliment to a WLAN professional's suite of analysis software. I can definitely say that consistent use of Eye P.A. strikes me as a very good way to gather basic information about your wireless channel usage in the same way that a consistent consumption of a normal IPA strikes me as a very good way to get throat cancer.
Amid all of our divisions over race, gender, religion and whether the Champions Bowl is going to be better than the Rose Bowl, we can agree one one thing: products named after alcohol are great. So you can imagine my excitement when I was made aware that Metageek -- hero to Windows users, villain to Mac users and tease to iPad users -- had introduced a WiFi sniffer.
Metageek is known 'round these parts ("round these parts" being, "in my opinion" ) as being a proprietor of low cost, attractive WLAN analysis tools. InSSIDer is the best active site surveying utility I've seen for Windows. The WiSpy/Chanalyzer combination is my spectrum analyzer of choice. (And I'll just choose to ignore the iPad tease that has been going to dang near a year now.) Eye P.A. is Metageek's entry into protocol analysis, and if nothing else it is quite unique.
Eye P.A. is different from most sniffers in that it doesn't sniff. Eye P.A. relies on saved capture files procured by other sniffers. Currently, the capture must be in the .pcap format and the capture must include an 802.11 Radiotap header. If you are a Linux or Mac user, a monitor mode capture from Wireshark will get you what you need. If you are a Windows user, you're going to need to spend at least seven hundred bucks on a Riverbed AirPcap NX USB adapter (or less than $700 on a cheaper AirPcap USB adapter, but then you'll miss 802.11n traffic).
Once a capture in the .pcap format (including 802.11 Radiotap) header is made, Eye P.A. will be able to open the file. Here is a screenshot showing what Eye P.A. looked like when I opened a capture that was taken from a hotel I was staying at a short while back:
The information is a little bit tricky to understand at first. There are three sets of circles; one for bytes, one for packets (actually, frames) and one for time. Each circle is actually a series of circles organized as follows:
- Inner circle: BSSIDs ( wireless MAC addresses of APs)
- Second circle: stations
- Third circle: frame types (management, control or data)
- Outer circle: frame subtypes
Each full circle represents 100% of what is in the capture. So, for example, in the screenshot above if my AP transmitted or received half of the bytes in my .pcap capture file, then my AP's BSSID would take up half of the innermost circle.
The idea of this design is to give WiFi folks a general idea of what's taking up channel space. That way if, for example, you are offering guest WiFi and you're wondering if it is bogging down your employee WiFi, you can do a quick .pcap capture, open the capture in Eye P.A. and quickly see the size of the partial circle that is labeled with the guest WiFi's BSSID.
Trent Cutler from Metageek (who deserves many thanks for giving me information on how Eye P.A.'s time calculations are done), also pointed out that Eye P.A. can be as good at quickly finding out whether there is a hidden node present as normal IPA is at giving you brain damage. On a channel without hidden nodes, the number of acknowledgment frames and data frames captured should be approximately equal, as seen in the Packets circles of this Eye P.A. view of my Macbook Air's traffic:
The bright orange area of the outer circle in the Packets view above are the acknowledgment frames for my laptop. The purple area of the outer circle in the Packets view are the data frames. Those two parts of the circle are about equal in size, indicating that my laptop is not a hidden node from the location where I captured. (That makes perfect sense, of course. I captured traffic using an AirPcap NX adapter that was attached to my laptop, so there is no way that my laptop's internal WiFI adapter would have been far enough away to be a hidden node.)
Eye P.A. does have usefulness in identifying hidden nodes and getting a general idea of what's taking up your channel space, but the big question is whether it is worth the $499 retail price. I think the software would be worth it for a lot of people who have to manage WiFi networks, but who feel overwhelmed by the amount of statistical information given by the average protocol analyzer. I especially like the Time circles, which use a method of calculation that factors in the amount of time taken up by the PLCP header. I could see someone who has a problem area just taking a Macbook to the problem area, doing a .pcap capture using Wireshark or Wi-Fi Diagnostics and then doing a few quick clicks or mouseovers to get a general idea of what could be the problem (over-deployment of APs, low rates to/from a station, hidden nodes, etc.). Then once Eye P.A. points someone in the right direction, a real-time WiFi sniffer like AirMagnet WiFi Analyzer or WildPackets OmniPeek could be used to pinpoint the problem and test whether an attempted solution works.
The bottom line is that Eye P.A. is a fine compliment to a WLAN professional's suite of analysis software. I can definitely say that consistent use of Eye P.A. strikes me as a very good way to gather basic information about your wireless channel usage in the same way that a consistent consumption of a normal IPA strikes me as a very good way to get throat cancer.

Comments
Post a Comment