iPhones Be Chatty

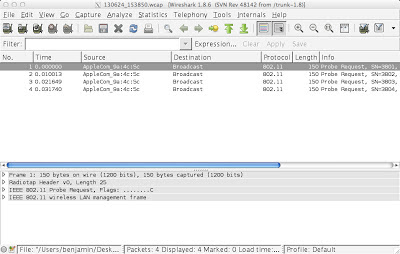
You'd think a great company like Apple would care about my privacy BUT NO. Behold, my iPhone: You see what's going on here? That's my iPhone there. Apple_57:8d:89. (Filtered using wlan.sa == f4:f1:5a:57:8d:89 if you're curious.) And look what it's doing. IT'S PROBING. The iPhone of a respected security do-gooder like myself is out there for any hooligan to see. Do I look like the type of person who wants the world to know that I used my phone at the MGM Signature in Las Vegas? (Well, maybe. I could've prevented the phone from probing by just tapping on the SSID instead of typing it in. But typing in SSIDs on iPhones/iPads is a neat trick for keeping stinky captive portal splash pages from coming up over and over again on guest WLANs.) Or on the VerizonWiFi network at Staples Center? (Which added a captive portal and lost A TON of guest connections, thus harming overall channel performance for all WiFi users in t...